Vocabulary Builder Activity
Students will learn the following key terms and phrases:
- Biometric authentication
- Botnet
- Brute force attack
- Chief Information Security Officer
- Compromise
- Credentials
- Cybersecurity specialist
- Data breach
- Exploit
- Joe job
- Multi-factor authentication
- Piggybacking
- Ransomware
- Replay attack
- Salami shaving
- Script kiddie
- Spoofing
- Tailgating
- Trojan horse
- Worm
- Zero-day
Reading Activity: Security Operations Center (SOC)
Students will be able to correctly answer true/false questions after reading and listening to topical short articles and dialogs featuring topical vocabulary.
Scene: It is 8:12AM in the SOC war room. Overnight, malware alerts have spiked sharply. A major client portal is timing out for some users in Europe. CISO: Good morning soldier! Bring me up to speed on the incident. SOC Analyst: Again, I am not really a soldier, but at 02:41 AM last night, our intrusion detection system flagged anomalous lateral movement from… Continue
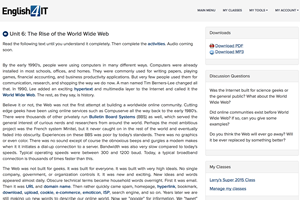
Multiple Choice Activity
Students will be able to select the best match between unit terms and their definitions.
You must sign in to try this activity.
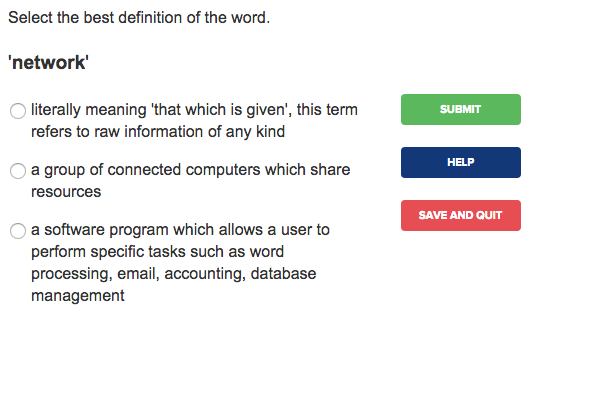
Listening Comprehension Activity
Students will be able to listen to short audio clips in English and then spell them correctly.
You must sign in to try this activity.
Spelling and Recognition
Students will be able to identify and spell a vocabulary term correctly given only the definition.
You must sign in to try this activity.
Speaking Practice Activity
Students will be able to speak and record 5 example sentences from the unit vocabulary and then submit them for grading by the classroom teacher. If no teacher is available or desired, then the students will be shown good examples of other students' work.
You must sign in to try this activity.
Writing Practice Activity
Students will write a short essay to be graded by the teacher. If no teacher is available or desired, then the student is shown previous examples of other writings by students.
You must sign in to try this activity.