Vocabulary Builder Activity
Students will learn the following key terms and phrases:
Reading Activity: The 10 Commandments of Computer Ethics
Students will be able to correctly answer true/false questions after reading and listening to topical short articles and dialogs featuring topical vocabulary.
Ethics is a branch of philosophy that deals with determining what is right and wrong. Listed below are 10 commandments to help you understand computer ethics. Anyone working in the field of IT is going to encounter a lot of ethical problems. Why? Because computers are very powerful and IT professionals are like wizards controlling this technology. We all know from watching Harry Potter movies that… Continue
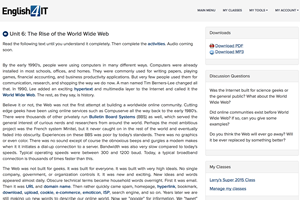
Multiple Choice Activity
Students will be able to select the best match between unit terms and their definitions.
You must sign in to try this activity.
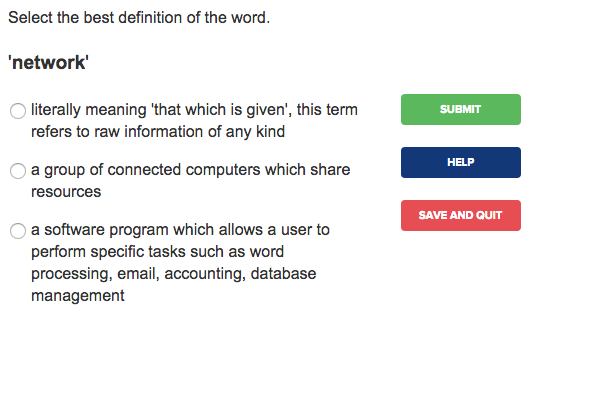
Listening Comprehension Activity
Students will be able to listen to short audio clips in English and then spell them correctly.
You must sign in to try this activity.
Spelling and Recognition
Students will be able to identify and spell a vocabulary term correctly given only the definition.
You must sign in to try this activity.
Speaking Practice Activity
Students will be able to speak and record 5 example sentences from the unit vocabulary and then submit them for grading by the classroom teacher. If no teacher is available or desired, then the students will be shown good examples of other students' work.
You must sign in to try this activity.
Writing Practice Activity
Students will write a short essay to be graded by the teacher. If no teacher is available or desired, then the student is shown previous examples of other writings by students.
You must sign in to try this activity.